
CYBER SYRUP
Delivering the sweetest insights on cybersecurity.
Unlock AI-powered productivity
HoneyBook is how independent businesses attract leads, manage clients, book meetings, sign contracts, and get paid.
Plus, HoneyBook’s AI tools summarize project details, generate email drafts, take meeting notes, predict high-value leads, and more.
Think of HoneyBook as your behind-the-scenes business partner—here to handle the admin work you need to do, so you can focus on the creative work you want to do.
ClickFix and TikTok Malware Campaigns: Latrodectus and Social Engineering in 2025
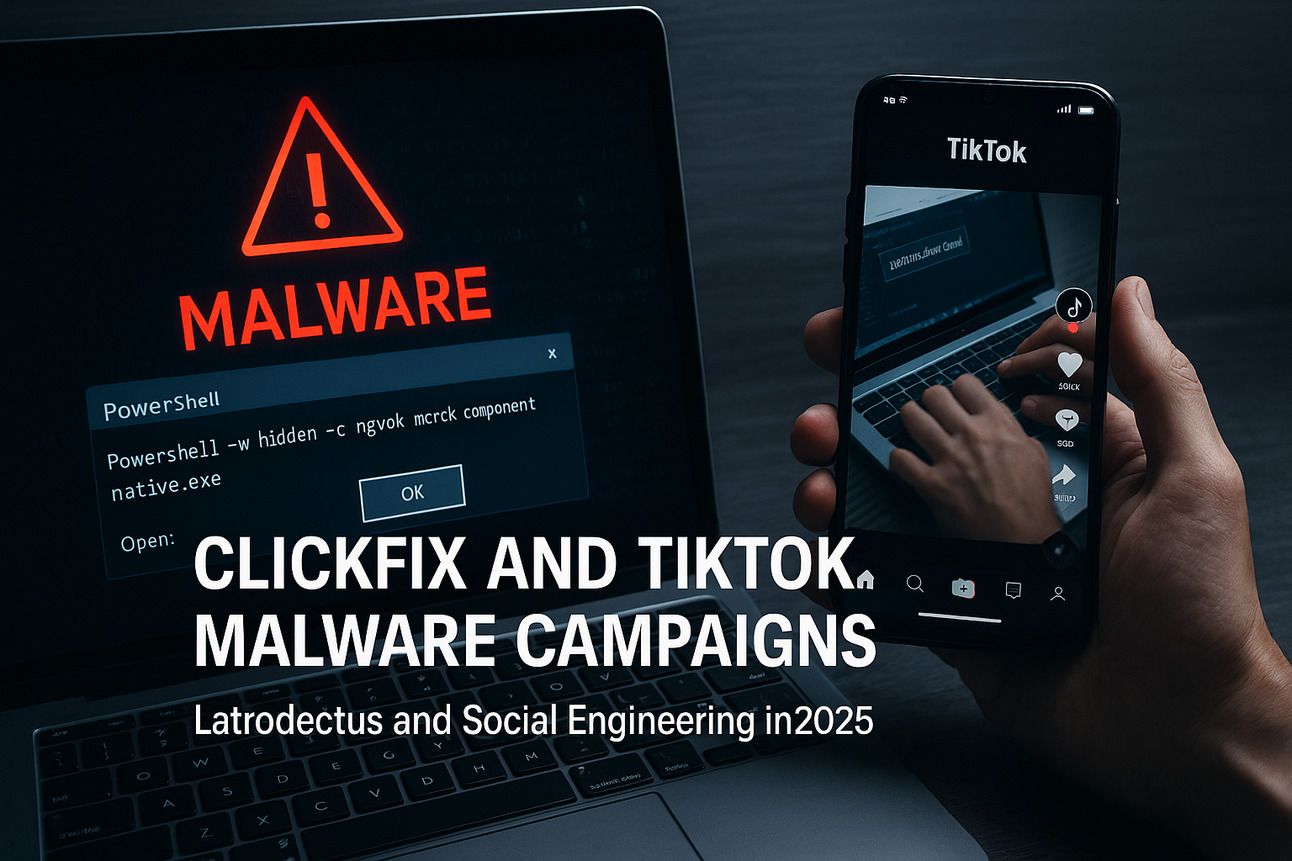
The cyber threat landscape continues to evolve with increasingly deceptive social engineering tactics. One of the most concerning developments is the integration of the ClickFix technique by the Latrodectus malware family—a downloader tool believed to be the successor of IcedID. This malware is now exploiting user behavior through cleverly crafted websites and even TikTok videos to deploy payloads without detection.
What Is Latrodectus?
Latrodectus is a modular malware loader first publicly detailed by Proofpoint and Team Cymru in April 2024. Like its predecessor IcedID, Latrodectus primarily serves as a delivery mechanism for more dangerous threats, such as ransomware and information stealers. Its ability to avoid detection and facilitate the execution of secondary malware makes it especially dangerous to organizations and individuals alike.
How ClickFix Works
The ClickFix technique relies on tricking users into manually executing malicious PowerShell commands, usually copied from a browser window and pasted into the Windows Run dialog or PowerShell terminal. This form of in-memory execution avoids writing files to disk, which makes detection by traditional antivirus tools more difficult.
“The ClickFix technique is particularly risky because it allows the malware to execute in memory rather than being written to disk,” said Expel, in a report.
In recent Latrodectus attacks observed in May 2025, victims were lured into running a PowerShell command that initiates the MSIExec installer. This downloads and runs a legitimate NVIDIA application, which then side-loads a malicious DLL. The DLL uses curl to retrieve the main payload—completing the infection without ever writing a visible executable to disk.
Operation Endgame’s Impact
It’s worth noting that Latrodectus was also among the malware families impacted by Operation Endgame, a global law enforcement effort that took place between May 19 and 22, 2025. This initiative successfully dismantled:
Over 300 servers
650 domains linked to malware like QakBot, TrickBot, Bumblebee, and Latrodectus
However, the appearance of new campaigns soon after demonstrates how adaptable and persistent these threat actors can be.
Expanding the Threat: TikTok as a Vector
In an alarming expansion of ClickFix tactics, Trend Micro recently uncovered a TikTok-based campaign delivering malware like Vidar and StealC—two powerful information stealers.
How It Works:
Threat actors publish TikTok videos claiming to help users activate pirated software (e.g., Spotify, Windows, CapCut).
These videos verbally and visually instruct users to:
Open the Windows Run dialog (
Windows + R)Launch PowerShell
Paste and run malicious commands
Commands then execute malware under the guise of software activation
The videos appear professionally made, and some have amassed hundreds of thousands of views, increasing the likelihood of widespread infection.
“Threat actors are now using TikTok videos that are potentially generated using AI-powered tools to socially engineer users into executing PowerShell commands,” explained researcher Junestherry Dela Cruz.
Notable TikTok Accounts Involved:
@gitallowed
@zane.houghton
@allaivo2
@sysglow.wow
@alexfixpc
@digitaldreams771
(All accounts are now deactivated.)
How to Protect Yourself
Whether targeted by ClickFix via websites or TikTok videos, users can take the following steps to avoid compromise:
Recommendations:
Disable Windows Run commands using Group Policy Objects (GPOs) or edit the Windows Registry to disable the "Windows + R" shortcut.
Avoid running PowerShell commands unless instructed by trusted IT personnel.
Use endpoint protection tools capable of detecting in-memory execution and suspicious process behavior.
Educate users on social engineering risks, especially those involving software cracks or "free upgrades" from unofficial sources.
Monitor social media trends for emerging attack vectors and update security policies accordingly.
Conclusion
The rise of Latrodectus and the expansion of ClickFix-style attacks onto platforms like TikTok reveal a shift in how malware is delivered in 2025. These campaigns rely less on sophisticated exploits and more on human error—emphasizing the critical role of user awareness and behavioral safeguards in modern cybersecurity.

