
CYBER SYRUP
Delivering the sweetest insights on cybersecurity.
Go from AI overwhelmed to AI savvy professional
AI keeps coming up at work, but you still don't get it?
That's exactly why 1M+ professionals working at Google, Meta, and OpenAI read Superhuman AI daily.
Here's what you get:
Daily AI news that matters for your career - Filtered from 1000s of sources so you know what affects your industry.
Step-by-step tutorials you can use immediately - Real prompts and workflows that solve actual business problems.
New AI tools tested and reviewed - We try everything to deliver tools that drive real results.
All in just 3 minutes a day
CVE-2025-6389: Critical WordPress Plugin Flaw Under Active Attack
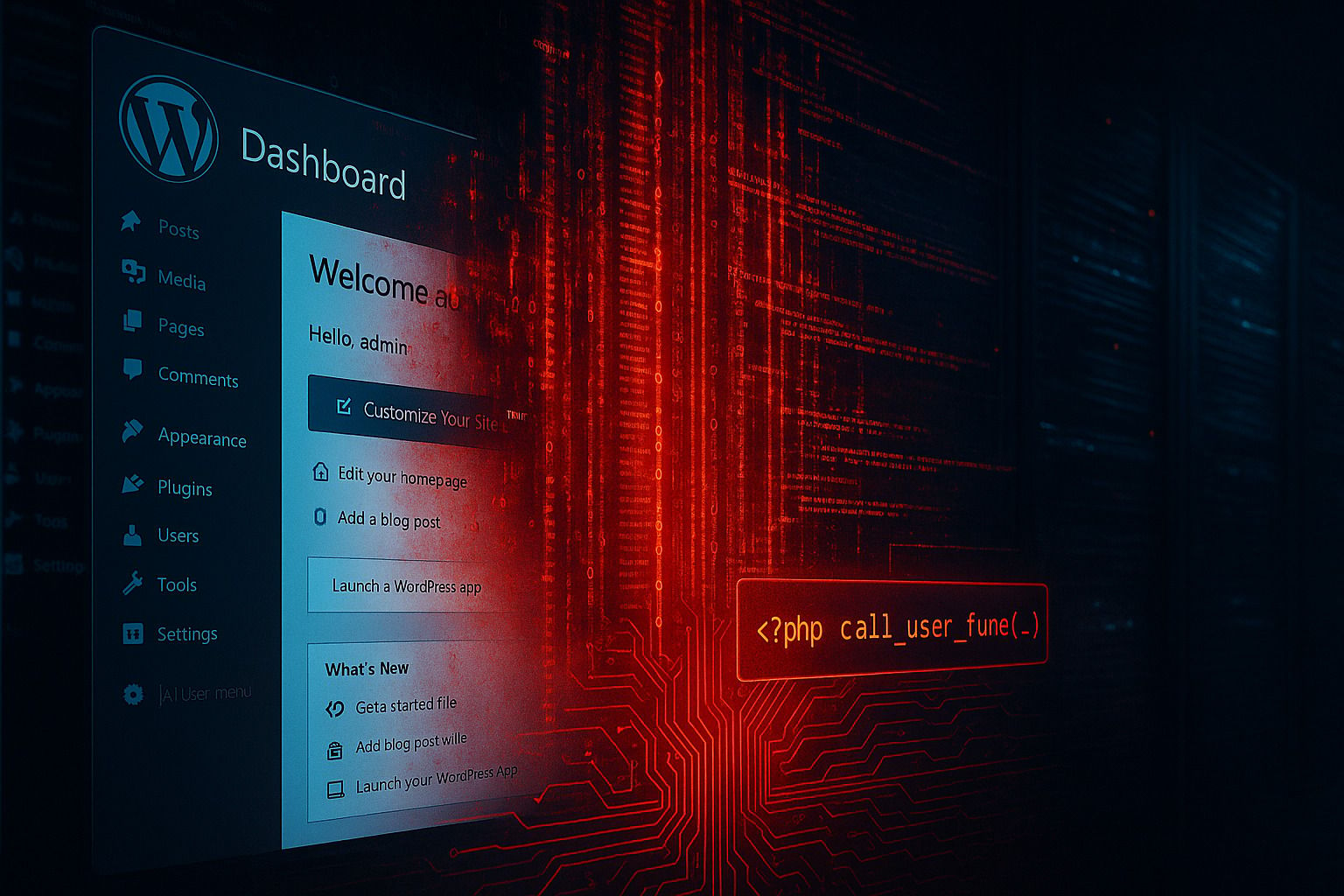
A critical remote code execution (RCE) vulnerability in the Sneeit Framework WordPress plugin (CVE-2025-6389, CVSS 9.8) is being heavily exploited in the wild. The flaw allows unauthenticated attackers to execute arbitrary PHP functions, create admin accounts, deploy backdoors, and take full control of affected websites. Over 131,000 exploitation attempts have been observed since disclosure.
Context
The Sneeit Framework plugin provides article pagination and layout functionality for WordPress themes. Although not a large-scale plugin, its 1,700+ active installations make it a valuable target for threat actors seeking direct server-side execution paths.
Wordfence threat intelligence confirms widespread automated exploitation began the same day the vulnerability was publicly disclosed.
What Happened
On November 24, 2025, a critical flaw in Sneeit Framework became publicly known. Attackers immediately began sending malicious requests to the WordPress admin-ajax.php endpoint to invoke vulnerable functionality.
Observed attacker objectives include:
Creating malicious administrator accounts
Uploading PHP backdoors
Deploying web shells for persistent access
Redirecting site visitors to malicious infrastructure
Scanning and modifying server files
Patch version 8.4 resolves the vulnerability; all earlier versions remain exploitable.
Technical Breakdown
The vulnerability resides in the function sneeit_articles_pagination_callback(), which:
Receives user-controlled input
Passes that input directly into
call_user_func()Enables execution of any PHP function without authentication
This allows attackers to run dangerous functions such as:
wp_insert_user()→ create new administrator accountsfile_put_contents()→ upload malicious filesunlink()→ delete critical files
Observed malicious artifacts include:
PHP shells:
xL.php,Canonical.php,.a.php,simple.phpLoader file:
up_sf.phpMalicious
.htaccessfromracoonlab[.]topBackdoor user accounts such as arudikadis
Key attacking IP addresses include:
185.125.50[.]59
182.8.226[.]51
89.187.175[.]80
194.104.147[.]192
196.251.100[.]39
114.10.116[.]226
116.234.108[.]143
Impact Analysis
If exploited, attackers can:
Fully compromise the WordPress site
Modify or delete content
Inject malware or redirection pages
Deploy persistent command-execution backdoors
Abuse the site for phishing, spam, or further propagation
Given the RCE nature, this vulnerability is equivalent to full server compromise on many shared hosting environments.
Why It Matters
This vulnerability demonstrates how even relatively small WordPress plugins can become high-impact attack vectors when they expose server-side execution mechanisms. The speed of exploitation—within hours of disclosure—highlights the modern threat landscape’s emphasis on rapid weaponization.
Expert Commentary
Wordfence emphasizes that the exploit chain is trivial and requires no authentication, making it highly attractive for both opportunistic and targeted attackers.
Their telemetry shows:
Over 131,000 exploitation attempts since disclosure
Over 15,000 attempts in the last 24 hours alone
This aligns with ongoing global patterns where RCE flaws in WordPress plugins become mass-exploitation events within hours.
Key Takeaways
CVE-2025-6389 is actively exploited and requires immediate patching to version 8.4 or newer.
The flaw enables unauthenticated RCE via
call_user_func()misuse.Attackers are deploying shells, backdoors, malicious users, and modified
.htaccessfiles.Incident response should include full file-system review, admin user audit, and log analysis.
Rapid exploitation underscores the need for automated WordPress patching strategies.

