CYBER SYRUP
Delivering the sweetest insights on cybersecurity.
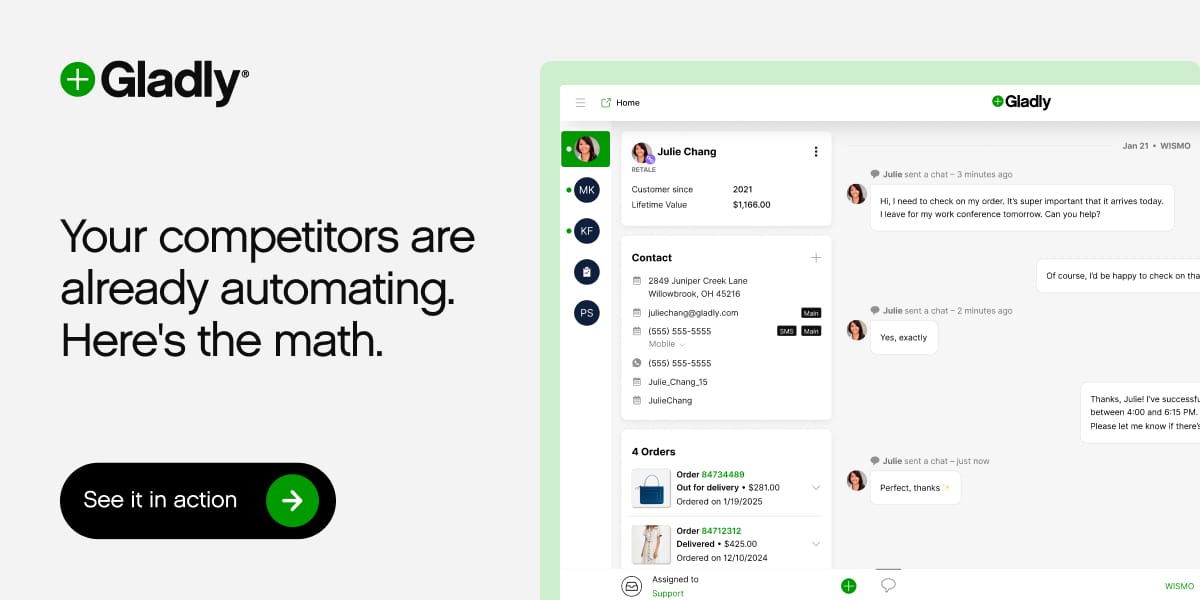
Your competitors are already automating. Here's the data.
Retail and ecommerce teams using AI for customer service are resolving 40-60% more tickets without more staff, cutting cost-per-ticket by 30%+, and handling seasonal spikes 3x faster.
But here's what separates winners from everyone else: they started with the data, not the hype.
Gladly handles the predictable volume, FAQs, routing, returns, order status, while your team focuses on customers who need a human touch. The result? Better experiences. Lower costs. Real competitive advantage. Ready to see what's possible for your business?
DOJ Indicts 54 in ATM Jackpotting Scheme Linked to Venezuelan Gang Tren de Aragua

The U.S. Department of Justice has indicted 54 individuals connected to a nationwide ATM jackpotting operation that used specialized malware to force cash withdrawals.
Authorities say the operation is tied to Tren de Aragua (TdA), a Venezuelan criminal organization designated as a foreign terrorist group by the U.S. government.
The scheme highlights how cyber-enabled crime can directly fund organized and transnational criminal activity, blending physical access with sophisticated malware.
Context
ATM jackpotting is a form of cyber-enabled theft where attackers compromise an ATM’s internal systems to dispense cash on command.
Unlike card skimming or fraud, jackpotting typically requires physical access to the machine and specialized malware designed to interact with ATM hardware.
Tren de Aragua has been linked to a wide range of criminal activities, including drug trafficking, extortion, human trafficking, and money laundering, making this case a notable intersection of cybercrime and terrorism financing.
What Happened
According to the DOJ, two indictments returned in October and December 2025 charged 54 individuals for their roles in the conspiracy.
Prosecutors allege that members and associates of Tren de Aragua conducted surveillance on ATMs, tested alarm responses, and then deployed malware to force machines to dispense cash.
The stolen funds were allegedly split among participants and funneled to TdA leadership to support broader criminal and terrorist activities.
Technical Breakdown
The attacks relied on malware known as Ploutus, a tool specifically designed to manipulate ATM cash dispensing modules.
Once physical access was achieved, attackers either replaced the ATM’s hard drive with a preloaded malicious drive or connected removable media containing the malware.
Ploutus can issue unauthorized commands directly to the ATM hardware, triggering cash withdrawals without legitimate transactions.
The malware also includes cleanup routines designed to erase traces of its presence, delaying detection by banks and service technicians.
Impact Analysis
U.S. authorities report more than 1,500 jackpotting incidents since 2021, resulting in losses exceeding $40 million as of August 2025.
Beyond direct financial losses, the attacks imposed operational costs on banks and credit unions, including machine downtime, forensic investigations, and infrastructure upgrades.
The scale and coordination of the operation demonstrate how cybercrime can be industrialized and geographically distributed.
Why It Matters
This case underscores how malware-enabled physical attacks can bypass traditional financial fraud controls.
It also illustrates the growing role of cyber techniques in funding organized crime and terrorism, elevating what might otherwise be viewed as “bank theft” into a national security concern.
For financial institutions, the threat extends beyond software vulnerabilities to physical security and insider risk.
Expert Commentary
“These defendants combined physical access, malware deployment, and money laundering to fund a designated terrorist organization,” said Acting Assistant Attorney General Matthew R. Galeotti.
Investigators note that the persistence of Ploutus—first observed over a decade ago—shows how legacy systems and outdated operating environments remain attractive targets.
Key Takeaways
ATM jackpotting blends physical access with specialized malware.
Ploutus malware enables direct manipulation of ATM cash dispensers.
The scheme allegedly funded a designated foreign terrorist organization.
Over $40 million has been lost in the U.S. since 2021.
Legacy ATM systems remain a high-risk attack surface.
Cybercrime increasingly intersects with organized and transnational crime.