
CYBER SYRUP
Delivering the sweetest insights on cybersecurity.
Receive Honest News Today
Join over 4 million Americans who start their day with 1440 – your daily digest for unbiased, fact-centric news. From politics to sports, we cover it all by analyzing over 100 sources. Our concise, 5-minute read lands in your inbox each morning at no cost. Experience news without the noise; let 1440 help you make up your own mind. Sign up now and invite your friends and family to be part of the informed.
Fake Antivirus Site Delivers Venom RAT and Stealer Tools in Modular Malware Campaign
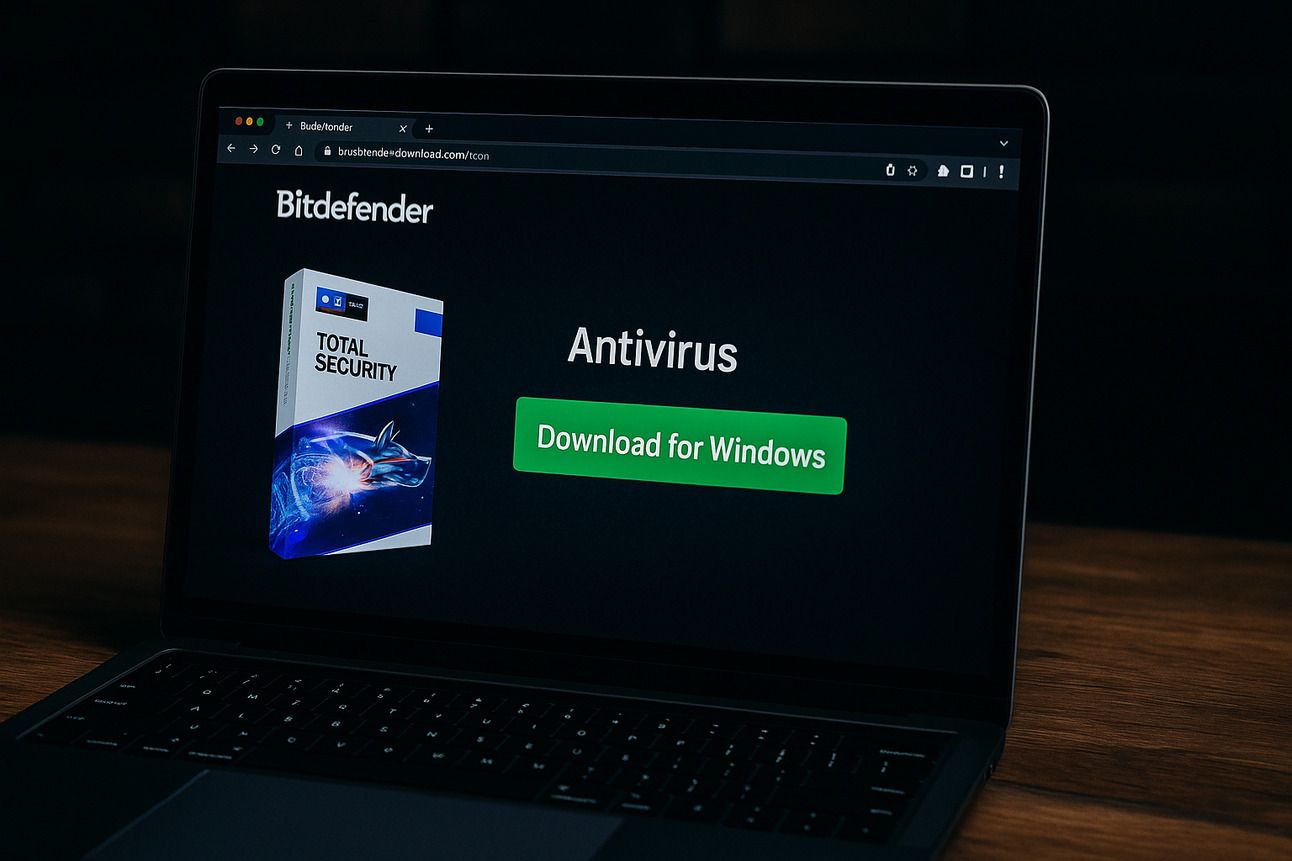
Cybersecurity researchers have uncovered a deceptive new malware campaign that uses a fake Bitdefender antivirus website to distribute a remote access trojan (RAT) known as Venom RAT, along with other modular components built from open-source malware tools. This campaign highlights the increasing use of social engineering and modular toolchains by attackers to compromise systems for financial gain.
The malicious site, bitdefender-download[.]com, impersonates Bitdefender’s legitimate antivirus software landing page. When visitors attempt to download the “Windows” version of the software, they are served a ZIP file hosted on an Amazon S3 bucket, following an initial redirect from a now-defunct Bitbucket repository.
Malware Components and Infection Chain
Inside the ZIP archive, labeled BitDefender.zip, is an executable named StoreInstaller.exe. This file is packed with:
Venom RAT – A Quasar RAT derivative that enables remote system control and persistent access.
StormKitty – An open-source information stealer designed to capture passwords, browser data, and cryptocurrency wallets.
SilentTrinity – A powerful post-exploitation framework that uses C# and PowerShell to maintain attacker access.
Coordinated Functionality
These tools work together to:
Harvest credentials and crypto wallet data (StormKitty)
Maintain persistent access to infected systems (Venom RAT)
Enable stealthy post-exploitation activities (SilentTrinity)
This modular architecture mirrors the growing trend in cybercrime where adversaries build custom malware using open-source frameworks. Such an approach allows for rapid deployment, stealth, and adaptability across various systems.
“This campaign underscores a constant trend: attackers are using sophisticated, modular malware built from open-source components,” said researchers at DomainTools Intelligence (DTI). “This ‘build-your-own-malware’ approach makes these attacks more efficient, stealthy, and adaptable.”
Infrastructure and Target Overlap
Researchers noted that the infrastructure behind this spoofed Bitdefender site shares similarities with domains previously used in phishing campaigns targeting:
Royal Bank of Canada
Microsoft accounts
Generic IT services
These overlaps suggest a shared operator or toolset, with a clear objective of credential harvesting and illicit system access resale.
Related Threats: ClickFix and AppSheet Abuse
The Venom RAT campaign arrives amid a broader wave of social engineering and phishing-based attacks.
Fake Google Meet Campaign
Sucuri recently reported a ClickFix-style scam using a spoofed Google Meet page that delivers a batch file (noanti-vm.bat) disguised as a fix for a "Microphone Permission Denied" error.
Victims are tricked into copying and executing a PowerShell command
The script downloads a remote access tool, granting attackers control
The deception avoids login credential harvesting and instead focuses on manual user execution
Phishing via Google AppSheet
A highly targeted phishing campaign leveraging Google’s AppSheet no-code development platform was detailed by KnowBe4 Threat Lab.
Emails spoof Facebook Support, warning of account deletion
Victims are urged to click a link within 24 hours to "appeal"
The link directs to an adversary-in-the-middle (AitM) phishing page
2FA tokens and credentials are harvested in real time
Technical Evasion Techniques
AppSheet’s use of legitimate domains (e.g.,
noreply@appsheet[.]com) helps bypass SPF, DKIM, and DMARC email filtersPolymorphic identifiers (e.g., unique “Case IDs” in each email) evade signature-based security solutions
“The presence of unique polymorphic identifiers in each phishing email ensures every message is slightly different,” KnowBe4 explained. “This helps them bypass traditional detection systems that rely on static indicators.”
Recommendations
To defend against these evolving threats, organizations and individuals should:
Verify URLs before downloading software or clicking on links
Avoid running scripts copied from unfamiliar sources, even if prompted by what appears to be a legitimate website
Deploy behavior-based endpoint detection systems that flag suspicious PowerShell and batch file activity
Educate users about phishing techniques, fake support pages, and MFA-related scams
Regularly patch browsers and systems, especially those used for handling financial or social media data
Conclusion
The Venom RAT campaign is a textbook example of modern malware operations, combining fake branding, modular toolkits, and open-source code to infiltrate and monetize compromised systems. As phishing and social engineering techniques continue to evolve, users must remain vigilant and adopt multi-layered defense strategies to stay ahead of such threats.

