
CYBER SYRUP
Delivering the sweetest insights on cybersecurity.
Find out why 1M+ professionals read Superhuman AI daily.
In 2 years you will be working for AI
Or an AI will be working for you
Here's how you can future-proof yourself:
Join the Superhuman AI newsletter – read by 1M+ people at top companies
Master AI tools, tutorials, and news in just 3 minutes a day
Become 10X more productive using AI
Join 1,000,000+ pros at companies like Google, Meta, and Amazon that are using AI to get ahead.
Malicious Chrome Extensions Campaign Discovered: What You Need to Know
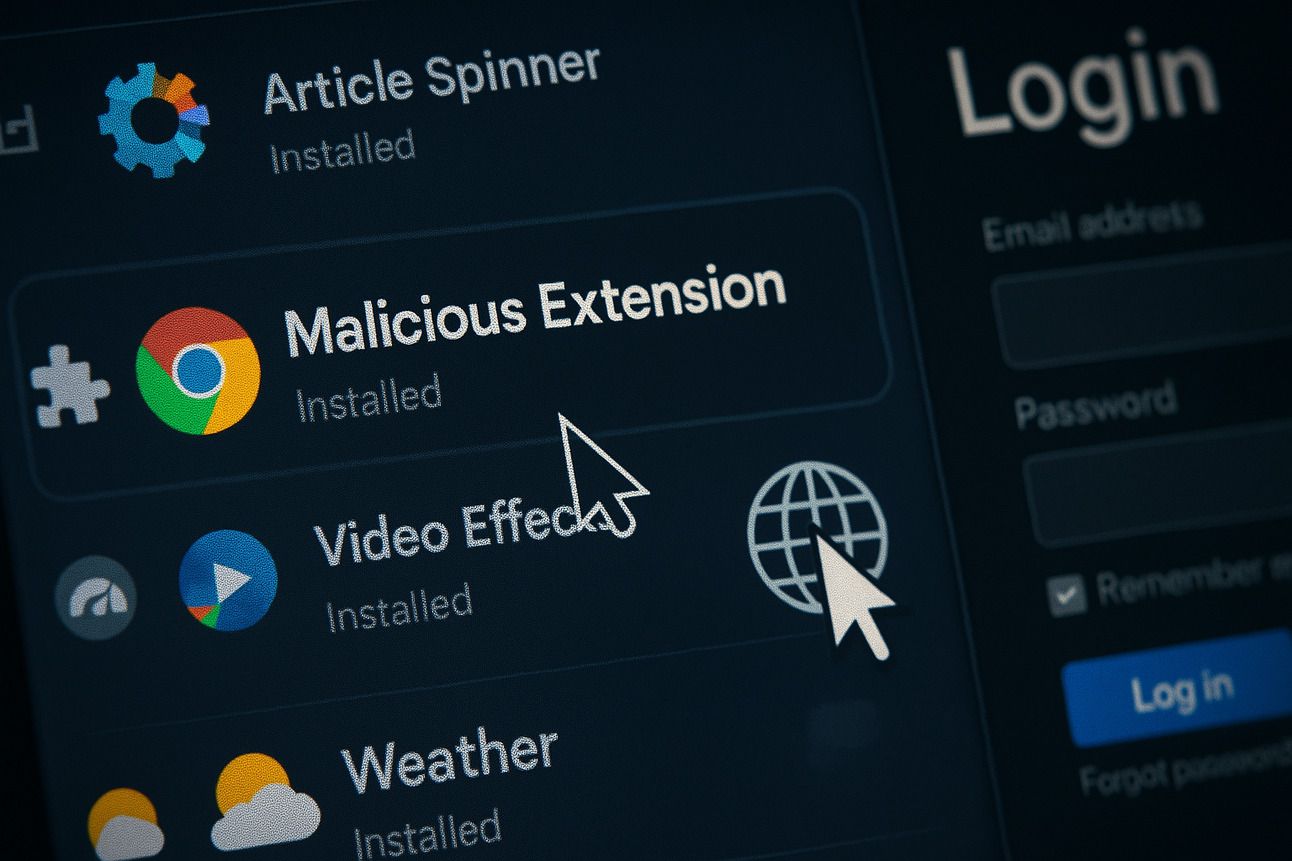
Cybersecurity researchers from DomainTools Intelligence (DTI) have uncovered a large-scale malicious campaign that has been active since at least February 2024. The campaign involves numerous Google Chrome extensions that are disguised as legitimate utilities but are in fact capable of stealing data, executing commands, and redirecting users to malicious destinations.
These extensions are part of a broader operation that lures users through deceptive websites and social engineering tactics, exploiting the trust placed in Chrome Web Store (CWS) listings.
How the Attack Works
The unknown threat actor behind the campaign has established a sophisticated operation:
Fake Websites: Over 100 bogus websites have been created to mimic legitimate services such as DeepSeek, DeBank, Manus, FortiVPN, and Site Stats.
Malicious Extensions: These sites prompt users to install related Chrome extensions, which are also uploaded to the Chrome Web Store under convincing names and descriptions.
Malicious Capabilities: Once installed, the extensions:
Steal cookies and credentials
Hijack browser sessions
Inject unauthorized ads
Redirect traffic to phishing sites
Execute arbitrary remote scripts
Manipulate the DOM for phishing or spoofing purposes
Technical Details
The extensions exploit browser APIs through overly permissive access grants found in their manifest.json configuration files. These permissions enable:
Access to all websites visited by the user.
Code execution from remote servers controlled by the attacker.
Redirection to harmful destinations.
Proxy behavior through WebSocket connections for traffic interception.
One particularly clever technique observed is the use of the "onreset" event handler on temporary DOM elements to circumvent browser Content Security Policies (CSP) and quietly load malicious code.
Distribution Channels
The exact delivery methods remain unclear, but evidence suggests a mix of strategies:
SEO manipulation: Because the malicious extensions are published on the Chrome Web Store and backed by standalone websites, they can appear in both standard web searches and Chrome extension searches.
Social Media Exploitation: DomainTools found that many lure websites include Facebook tracking IDs, suggesting attackers may be leveraging:
Facebook groups
Facebook pages
Paid advertisements on Meta platforms
These methods increase the likelihood of unsuspecting users visiting the sites and downloading malicious extensions, especially when extensions are presented as productivity tools, VPNs, or AI utilities.
Google's Response
As of the time of reporting, Google has removed the malicious extensions from the Chrome Web Store. However, the number of fake domains and the sophistication of the campaign suggest that the threat actor is likely to resurface with new tactics or domains.
Recommendations for Users
To stay protected from similar threats, users should take the following precautions:
Install from Verified Developers: Only install extensions from well-known or verified publishers.
Check Permissions Carefully: Be wary of extensions asking for permissions unrelated to their advertised purpose.
Scrutinize Reviews: Look for inconsistencies in ratings and read reviews thoroughly. Keep in mind:
Ratings can be manipulated.
Malicious extensions in this campaign redirect low-star reviewers to a private form and only allow high-star reviewers to post on the Chrome Web Store.
Limit Browser Extensions: Remove any unnecessary extensions and monitor changes in browser behavior.
Report Suspicious Activity: Report extensions or websites you believe to be harmful directly to Google.
Final Thoughts
This campaign highlights a troubling trend where browser extensions—once thought of as simple productivity tools—are being weaponized to compromise user privacy and security. The use of social engineering, trusted brand impersonation, and browser vulnerabilities demonstrates a multi-layered approach by threat actors aiming to infiltrate systems with minimal detection.
As cybersecurity threats continue to evolve, it’s essential for users and organizations alike to practice due diligence, maintain awareness, and implement layered defenses that go beyond antivirus tools. In today’s landscape, even a browser extension can become a significant attack vector.

