
CYBER SYRUP
Delivering the sweetest insights on cybersecurity.
Not All AI Notetakers Are Secure. Here’s the Checklist to Prove It.
You wouldn’t let an unknown vendor record your executive meetings, so why trust just any AI?
Most AI notetakers offer convenience. Very few offer true security.
This free checklist from Fellow breaks down the key criteria CEOs, IT teams, and privacy-conscious leaders should consider before rolling out AI meeting tools across their org.
Malicious Firefox Extensions Stealing Crypto Wallet Secrets
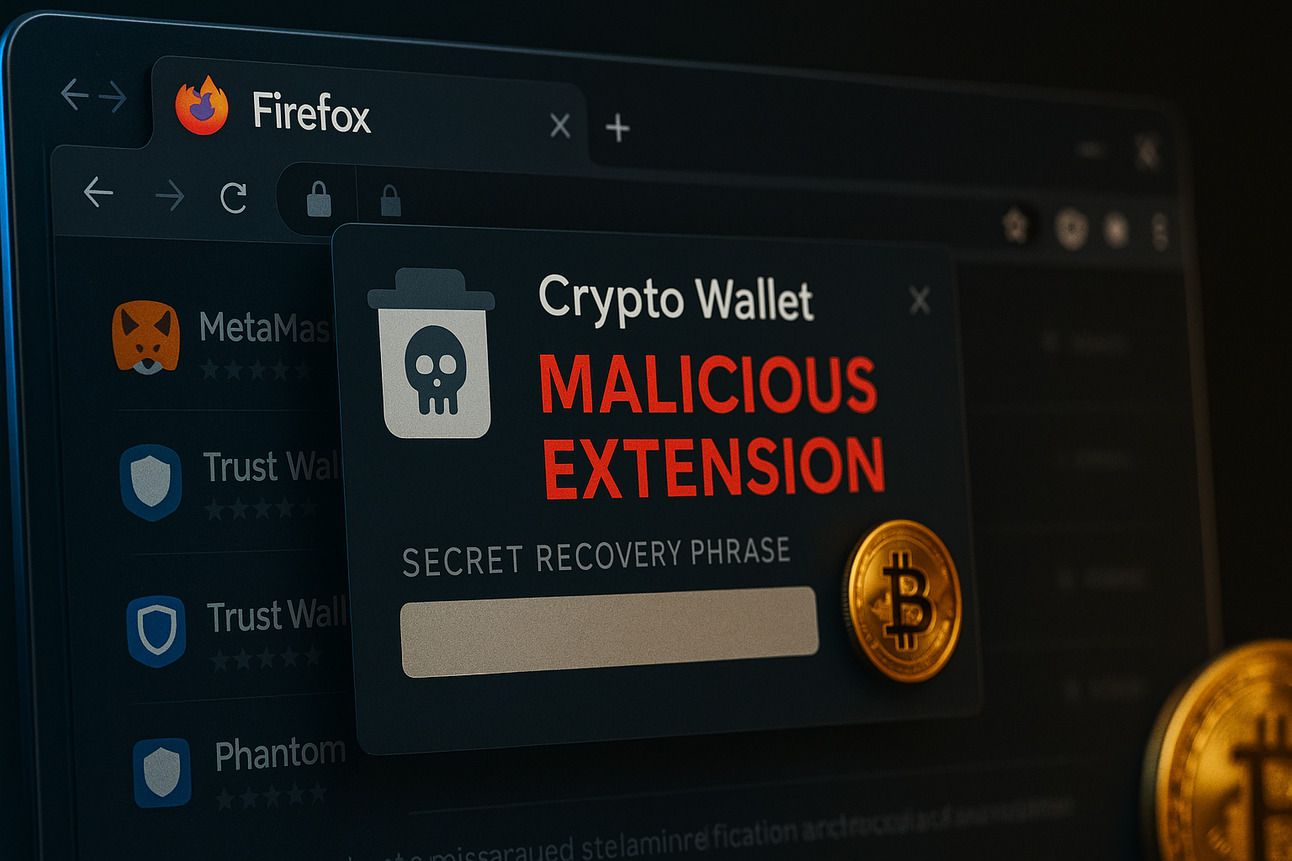
Cybersecurity researchers have uncovered over 40 malicious browser extensions on the Mozilla Firefox Add-ons store designed to steal cryptocurrency wallet credentials. These extensions impersonate legitimate wallet tools—including Coinbase, MetaMask, Trust Wallet, Phantom, Exodus, OKX, Keplr, MyMonero, Bitget, and others—putting users’ digital assets at serious risk.
According to Yuval Ronen of Koi Security, the campaign has been active since at least April 2025, with some extensions uploaded as recently as last week.
How the Attack Works
These rogue extensions:
Mimic real crypto wallet tools by using the same logos and names.
Clone open-source code of legitimate extensions, embedding malicious scripts that extract private keys and seed phrases.
Exfiltrate user data, including wallet secrets and external IP addresses, to attacker-controlled servers.
Artificially boost credibility by adding hundreds of fake 5-star reviews, making them seem trustworthy despite few real users.
The result is a browser-based threat that bypasses traditional phishing methods and operates inside the user’s browser environment, making detection far more difficult.
“This low-effort, high-impact approach allowed the actor to maintain expected user experience while reducing the chances of immediate detection,” said Ronen.
Attribution and Response
Analysis of code comments and command-and-control (C2) metadata suggests a Russian-speaking threat actor group is behind the campaign. Mozilla has removed nearly all identified malicious extensions—except for MyMonero Wallet, which remains under review.
In response to this incident and similar threats, Mozilla has introduced an early detection system designed to catch scam crypto extensions before they become widespread.
What Users Can Do
To reduce the risk of compromise, users should:
Only install browser extensions from verified and reputable publishers.
Avoid extensions that seem too new, have low install counts, or disproportionately high ratings.
Review permissions carefully before installing.
Regularly audit installed extensions for suspicious behavior.
Final Thoughts
This discovery underscores the growing sophistication of crypto-targeted attacks within trusted platforms like the Firefox Add-ons ecosystem. As attackers adapt by moving malware into browser extensions, users must remain vigilant and cautious—even when visiting official extension stores.

