CYBER SYRUP
Delivering the sweetest insights on cybersecurity.
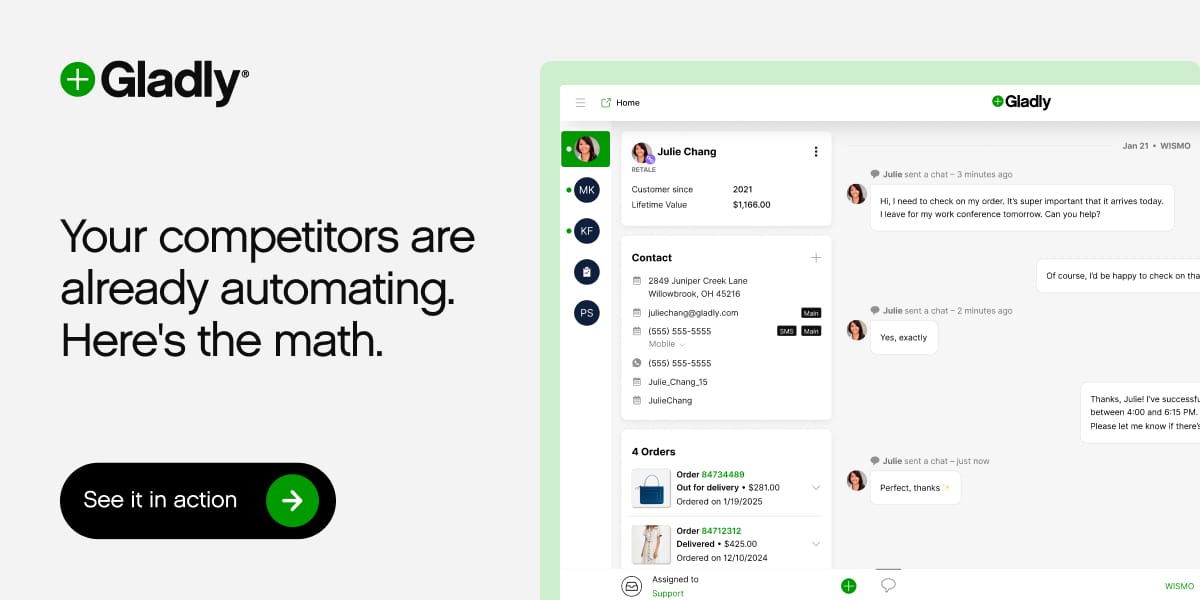
Your competitors are already automating. Here's the data.
Retail and ecommerce teams using AI for customer service are resolving 40-60% more tickets without more staff, cutting cost-per-ticket by 30%+, and handling seasonal spikes 3x faster.
But here's what separates winners from everyone else: they started with the data, not the hype.
Gladly handles the predictable volume, FAQs, routing, returns, order status, while your team focuses on customers who need a human touch. The result? Better experiences. Lower costs. Real competitive advantage. Ready to see what's possible for your business?
State Government Websites Abused in SEO Poisoning Campaign

A widespread SEO poisoning campaign has abused trusted U.S. state and local government websites to distribute illicit advertisements and malware-linked content through Google search results. Rather than exploiting traditional software vulnerabilities, attackers leveraged legitimate public upload mechanisms to seed AI-generated pornography ads, scam content, and malicious links across dozens of official government domains. The incident highlights a growing class of “trust abuse” attacks that weaponize credibility instead of breaking security controls.
Context
Government websites are highly trusted by search engines and users alike. Their domains carry strong reputational signals, making them attractive targets for SEO manipulation. Many public-sector platforms include features such as feedback forms, document uploads, and event calendars designed to encourage civic engagement. When these features are insufficiently restricted or moderated, they can become powerful tools for attackers seeking visibility rather than persistence.
What Happened
Beginning in late November, researchers and journalists identified illicit content appearing in Google search results under official state and municipal domains. At least 38 agencies across 18 U.S. states—and several international jurisdictions—were affected.
The content included AI-generated pornography ads, fake “AI nude” tools, explicit videos, sex toy promotions, cryptocurrency scams, video game cheats, and links to potentially malicious downloads. High-profile affected entities included state health departments, transportation agencies, museums, and federal organizations.
Security researcher Dominic Alvieri and journalist Brian Penny independently documented the campaign, sharing evidence of PDF files and media uploaded directly to government-hosted platforms.
Technical Breakdown
Crucially, investigators found no evidence that the affected government websites were hacked.
Instead, attackers exploited legitimate public submission features—such as feedback forms, calendar uploads, and document attachments—to upload illicit files. These files were then automatically indexed by search engines, causing them to surface prominently in search results due to the inherent trust of government domains.
In some cases, bot-driven activity abused group calendars or submission portals from a limited number of IP addresses. The hosting provider Granicus, which supports roughly 5,500 government websites, confirmed the issue stemmed from content abuse rather than a breach of its infrastructure.
Impact Analysis
While core systems and sensitive data were not compromised, the reputational damage is significant. Government agencies appeared—unintentionally—to endorse explicit or malicious content. This undermines public trust, exposes users to potential malware, and burdens agencies with incident response and remediation efforts.
The campaign also demonstrates how attackers can achieve large-scale distribution without exploiting vulnerabilities, relying instead on search engine dynamics and platform design assumptions.
Why It Matters
This incident reflects a shift in attacker strategy. Rather than breaking in, adversaries are increasingly “checking in” through allowed features and abusing automation, indexing, and trust.
For public-sector organizations, this blurs the line between content moderation, security, and platform governance. Traditional security controls alone are insufficient to prevent this class of attack.
Expert Commentary
The campaign illustrates a modern form of supply-chain and trust abuse. By leveraging legitimate workflows, attackers bypass many detection mechanisms and avoid triggering breach alerts.
Security teams must treat public-facing content ingestion pipelines as attack surfaces, applying the same rigor used for authentication, APIs, and software updates.
Key Takeaways
Government websites were abused via legitimate upload features, not hacked
Attackers seeded illicit PDFs and media to poison search results
Trusted domains amplified the visibility of malicious and explicit content
SEO poisoning increasingly relies on trust abuse rather than exploits
Content moderation and upload controls are now security-critical
Blocking execution is not enough—indexing and visibility must be managed