CYBER SYRUP
Delivering the sweetest insights on cybersecurity.
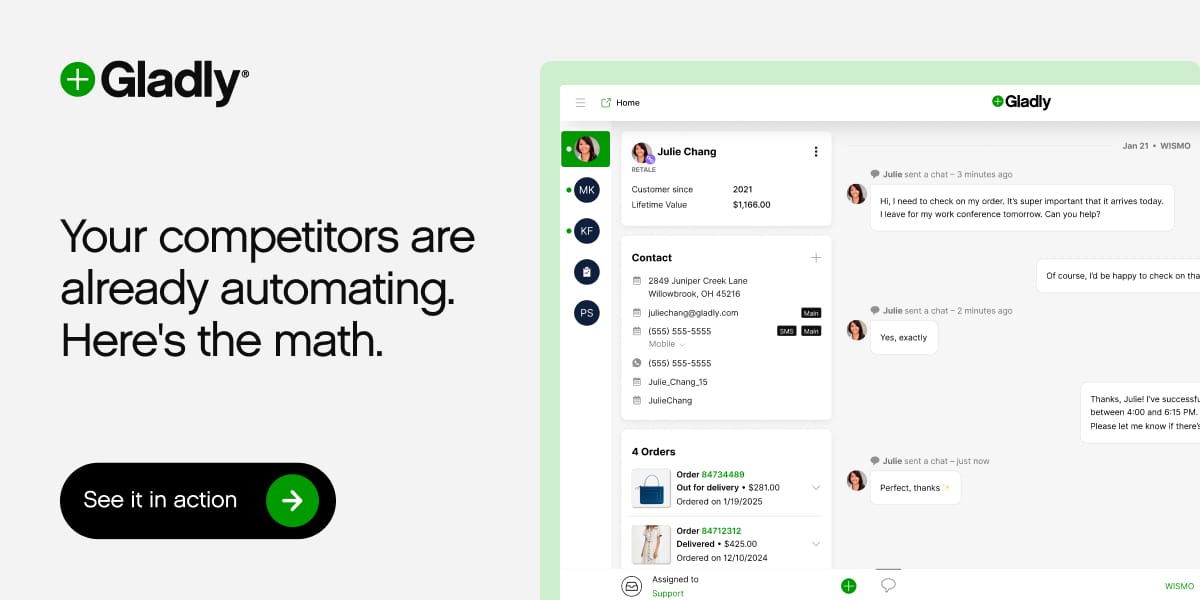
Your competitors are already automating. Here's the data.
Retail and ecommerce teams using AI for customer service are resolving 40-60% more tickets without more staff, cutting cost-per-ticket by 30%+, and handling seasonal spikes 3x faster.
But here's what separates winners from everyone else: they started with the data, not the hype.
Gladly handles the predictable volume, FAQs, routing, returns, order status, while your team focuses on customers who need a human touch. The result? Better experiences. Lower costs. Real competitive advantage. Ready to see what's possible for your business?
“WhiteLeaks” Exposes Extremist Dating Networks After Major Data Exfiltration

An investigative journalist operating under the pseudonym Martha Root has exfiltrated more than 100GB of data and over 8,000 user profiles from multiple white supremacist online platforms, exposing severe security failures and extensive personal data leakage.
The dataset—dubbed “WhiteLeaks”—has been made available to journalists and researchers via Distributed Denial of Secrets (DDoSecrets). The incident highlights how poor cybersecurity practices, combined with basic automation and scraping techniques, can lead to large-scale exposure of extremist communities operating online.
Context
Extremist groups increasingly rely on mainstream web technologies to organize, recruit, and socialize.
Dating and networking platforms, in particular, offer ideological communities a veneer of normalcy while facilitating relationship-building and coordination. These sites often operate outside regulatory scrutiny and are frequently maintained by small operators with limited security expertise.
As a result, they can become prime targets for investigative research, OSINT collection, and data exposure.
What Happened
Root infiltrated WhiteDate, a white supremacist dating platform, along with two related sites: WhiteChild and WhiteDeal.
All three platforms were operated by a right-wing extremist based in Germany and were allegedly managed through a Paris-based company, Horn & Partners. The sites catered to users promoting racist ideologies, framing themselves as spaces for dating, family-building, and professional networking.
After months of observation and data collection, Root exfiltrated the full user databases. The exposed information has since been mapped and partially visualized through a separate website, revealing users distributed across multiple countries.
Technical Breakdown
The compromise did not require exploitation of advanced vulnerabilities.
Root initially created fake user accounts using locally run large language models via Ollama. These AI-driven profiles successfully bypassed platform verification checks and were even marked as “verified.”
Data collection combined automated conversation analysis, classic OSINT techniques, and web scraping. According to Root, full database access was enabled by a simple URL path manipulation, allowing bulk user downloads without authentication. No traditional hacking tools were required.
Critically, many uploaded images retained EXIF metadata, exposing GPS coordinates, device identifiers, and timestamps—information that can directly reveal home locations and daily routines.
Impact Analysis
The exposed dataset contains deeply sensitive, self-reported information, including:
Real names and usernames
Precise locations
Physical traits and photos
Education, income, and family status
Religious beliefs and self-assessed IQ
While private messages and emails have not been publicly released, the scale and granularity of the exposed data pose serious personal safety and privacy risks to individuals listed in the dataset.
The incident also demonstrates how extremist platforms may unintentionally create intelligence troves through negligence.
Why It Matters
This case underscores how poor security hygiene can dismantle secrecy-dependent extremist networks.
It also highlights the growing role of AI-assisted social engineering in investigative research. The same techniques used here for antifascist documentation could be repurposed maliciously in other contexts, raising broader questions about platform verification, automation abuse, and ethical boundaries.
Expert Commentary
Root and collaborating journalists presented their findings at the Chaos Communications Congress, emphasizing that the operation revealed not just ideological extremism, but technical incompetence.
The research illustrates how minimal safeguards can collapse under sustained scrutiny—and how ideology offers no protection against basic cybersecurity failures.
Key Takeaways
Over 8,000 extremist profiles and 100GB of data were exfiltrated
Platforms suffered from severe, basic security flaws
AI-driven fake accounts bypassed verification systems
EXIF metadata exposed precise user locations
Data is now accessible to journalists via DDoSecrets
No advanced hacking was required—only poor design